What is callback phishing?
At its core, callback phishing is a sophisticated social engineering tactic that triggers an emotional reaction from a victim and compels them to take an action. Instead of directing them to click a suspicious link or download a malicious attachment like traditional social engineering, these scams cleverly prompt the victim to dial a phone number.
Although commonly underestimated as low-level nuisances, the repercussions of falling for such scams can be catastrophic.
For individuals, it can lead to devastating financial losses such as depleted life savings or drained retirement accounts. For businesses, callback phishing can lead to malware/ransomware delivery and any number of follow-on intents including financial or data theft.

What makes detection hard?

Detecting callback phishing is challenging because attackers employ a number of novel Tactics, Techniques, and Procedures (TTPs) to evade security tools.
First and foremost, there is no traditional URL or attachment payload. Just a phone number.
Second, the phone numbers, which are essentially the "payload," are often cleverly hidden or obfuscated. They can be embedded in the email body, tucked away in a PDF attachment, or even concealed within an image. This makes automated extraction and identification difficult or unreliable.
Third, the templates used in these messages are ephemeral. Their contents and formatting change rapidly, sometimes within hours, making it difficult to keep track of threat patterns.
Next, the use of Images as Content means traditional text based content analysis won't work.
Traditional domain based reputation isn't a useful signal, since over 90 percent of the attacks we've observed use freemail accounts. We see a variety of freemail providers used, but Gmail is by far the most common.
To make attacks more convincing, attackers impersonate well known brands like Best Buy or Norton. Sometimes they use text in an image, and other times they embed the brand's logo making traditional text based analysis ineffective.
Last but not least, the use of VoIP services allows attackers to frequently switch phone numbers, rendering traditional "known bad" lists ineffective.
These factors collectively create a complex landscape that makes callback phishing a particularly elusive threat to tackle.
Detection Techniques
With an understanding of attacker TTPs, we can start to think about detection strategies.
Let's start with one of the simplest variants. In this attack, the text is embedded directly in the body of the message. How would we detect this?

Body-based Text Detection: String Analysis
If the attack is in the text body of the message, such as the `text/html` or `text/plain` sections, it can be relatively straightforward to detect. In this Sublime Detection Rule, we leverage the following signals:
- Freemail sender. We maintain an open-source list of over 23,000 freemail providers.
- Brand impersonation. We look for common brands including Norton, Geek Squad, and PayPal using simple text based analysis of the message body
- Tone and intent. A sense of urgency and call to action.
- Organization specific historical context. Do we know this sender? Have we corresponded with them before?

This is as simple as it gets. It's straightforward, yet highly effective, which is a testament to Message Query Language (MQL). To detect more sophisticated variants and be more resilient to bypass, we'll need to incorporate more advanced detection techniques.
Image-based Text Detection: Computer Vision + NLU
What if the attack was embedded entirely in an image attachment? For image-as-content attacks, Optical Character Recognition (OCR), a form of Computer Vision, is key to extracting text from images before applying detection logic.
In this Sublime Detection Rule, we first run OCR to extract text from the attachment, then leverage the following signals:
- "Callback Phishing Scam" tone and intent with High confidence, as classified by our Natural Language Understanding (NLU) model. This Machine Learning model has been trained on tens of thousands of callback phishing emails to recognize attack tone and intents, urgency, sense of loss or expiration, common brands, phone numbers, and much more.
- Organization specific historical context. Do we know this sender? Have we corresponded with them before?
For more on our NLU model, check out Unmasking BEC attacks using Natural Language Understanding + MQL.
Note that in this detection, we aren't limiting to freemail senders. Since we have higher fidelity with OCR and NLU on an image attachment, we can expand our scope to include custom domains without the risk of egregious false positives.

Image-based Logo Detection: Computer Vision
What if the elements of the brand impersonation are in a logo, opposed to strings in the body or in an image? In a previous post, we discussed how we use Deep Learning to detect Credential Phishing. We can use the same Deep Learning / object detection models to identify known brand logos in message bodies and attachments.
Let’s review the following attack where a well recognized brand is being impersonated.
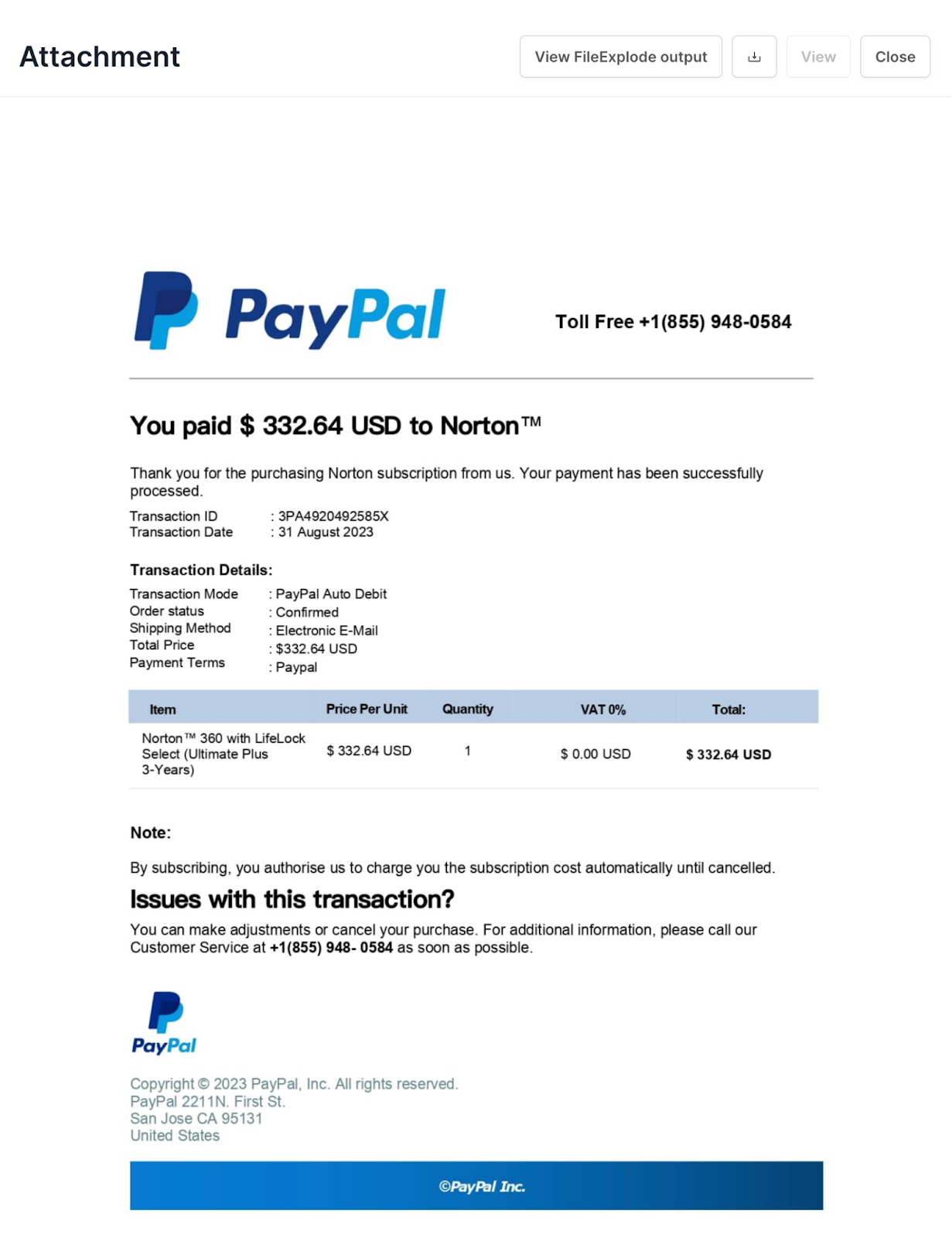
In this Sublime Detection Rule, we leverage the following signals:
- PayPal brand logo in an image or PDF attachment
- Sender impersonation
- Lookalike domain
- Suspicious text extracted from the attachment using OCR
- Organization specific historical context.

While we've just scratched the surface, you can start to see how Computer Vision and other Machine Learning techniques play a key role in detecting and preventing these elusive attacks. All of the above detection rules are open source and included in any free or paid Sublime deployment.
Attacker Intents
What do adversaries aim to achieve with these attacks? Once an attacker gets a user on the phone, common objectives include malware/ransomware delivery for financial or data theft.
They'll often talk the user through downloading and installing malware or commercial remote access tools disguised as “support” tools. These could be tools such as LogMeIn or another legitimate binary that's used commercially. We've seen modified remote access trojans (RATs) used too. For personal financial theft, we've seen attackers blank the user's screen while logged into their bank account, and just start transferring money out. It's very sad to read about these stories.
Evolution of Callback Phishing
Scambaiting and Countermeasures
Callback phishing, and really any form of financially motivated cybercrime, is a numbers game. It's about maximizing Return on Investment (ROI). The more we can raise the cost, the better chances we have at flipping that equation and forcing attackers elsewhere.
To that affect, Twitch streamers like Kitboga and even security researchers are wasting attackers’ time by baiting them into a conversation and exposing them online ("scambaiting"). They've done this to dozens of attackers, and it also serves as a form of education for the community.
To combat this, we've seen attackers evolve in form and begin to implement their own countermeasures like multi-factor authentication requirements by the original recipient of the attack.
Case Study: Engaging with Callback Phishing Attacks
For research purposes, we called one of these numbers to observe a phishing attempt.
The first thing they had us do is navigate to a legitimate domain (logmeinrescue.com) and input a multi-factor authentication code that was sent to our email. They sent the code to the email address of the original attack to verify that it was actually us—their scam baiting countermeasure.

After verification, we installed the legitimate LogMeIn rescue binary.

Then we were asked to initiate a screen share with the attacker.

Within minutes, they showed us that we were "hacked" with 30 plus "hackers" connected to our machine 😄

In order for them to rid us of these hackers, we had to route them money as a support fee.
That's when we ended the call.
The Future of Callback Phishing
While we can't predict what exactly the next variant of callback phishing will look like, what we can count on are continuously advancing techniques from scammers. Callback phishing will continue to evolve so long as it remains a good business.
Watch the original talk at SleuthCon 2023 here.
-----
Deploy a free Managed or Self-Managed instance of Sublime today to prevent these attacks. No MX changes required.

